#ChaosDB is an unprecedented critical vulnerability in the Azure cloud platform that allows for remote account takeover of Azure’s flagship database - Cosmos DB. The vulnerability, which was disclosed to Microsoft in August 2021 by Wiz Research Team, gives any Azure user full admin access (read, write, delete) to another customers Cosmos DB instances without authorization. The vulnerability has a trivial exploit that doesn't require any previous access to the target environment, and impacts thousands of organizations, including numerous Fortune 500 companies.
We added a detailed section in our blog regarding Protecting your environment from ChaosDB.
By exploiting a chain of vulnerabilities in the Jupyter Notebook feature of Cosmos DB, a malicious actor can query information about the target Cosmos DB Jupyter Notebook. By doing so, the attacker will obtain a set of credentials related to the target Cosmos DB account, the Jupyter Notebook compute, and the Jupyter Notebook Storage account, including the Primary Key. Using these credentials, it is possible to view, modify, and delete data in the target Cosmos DB account via multiple channels. Below is a diagram that illustrates the attack.
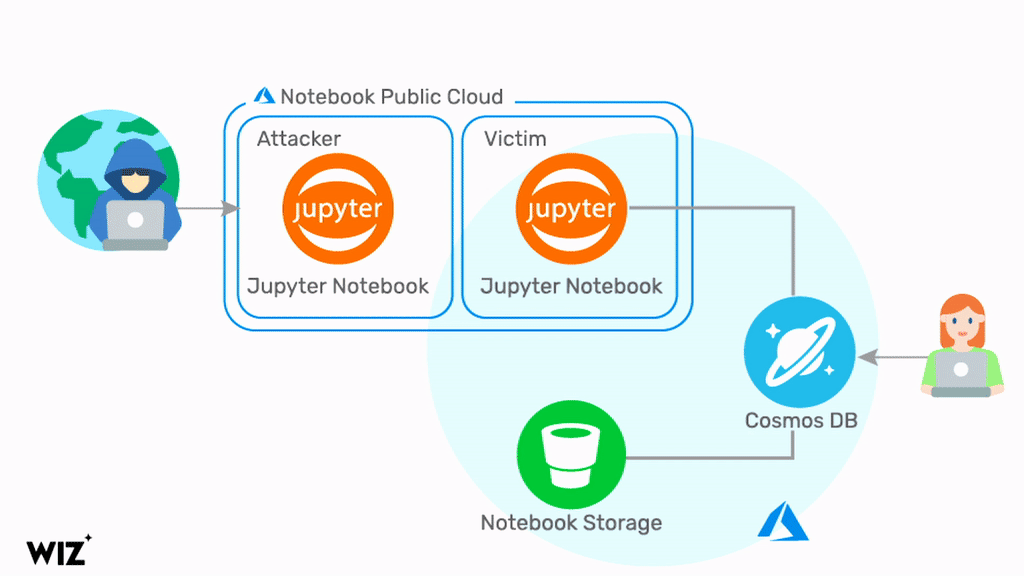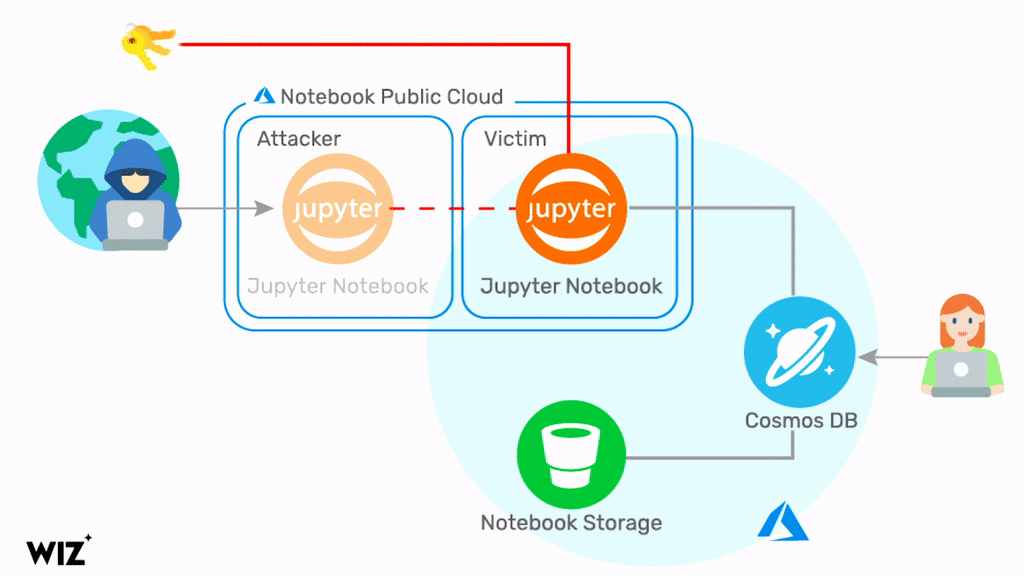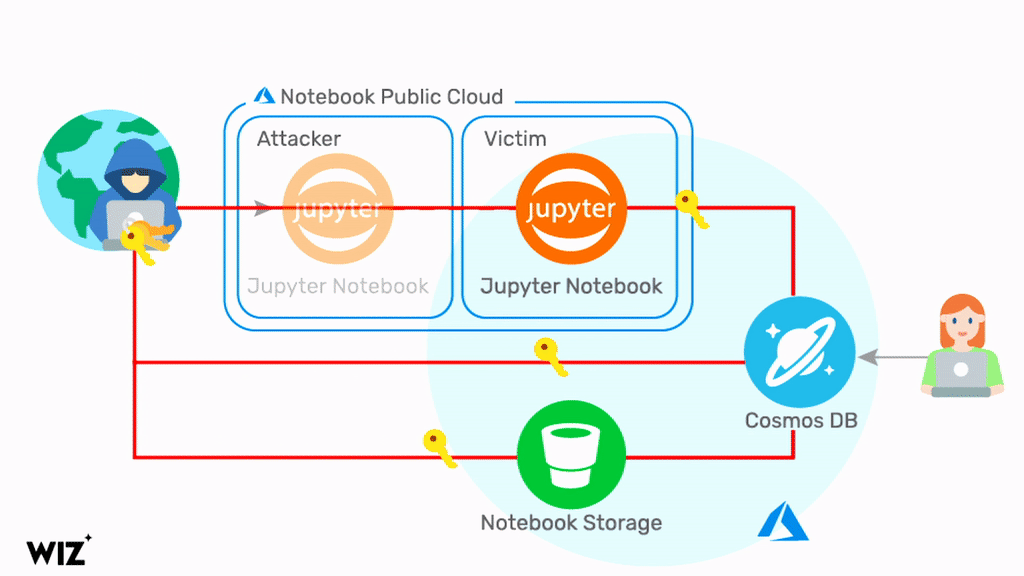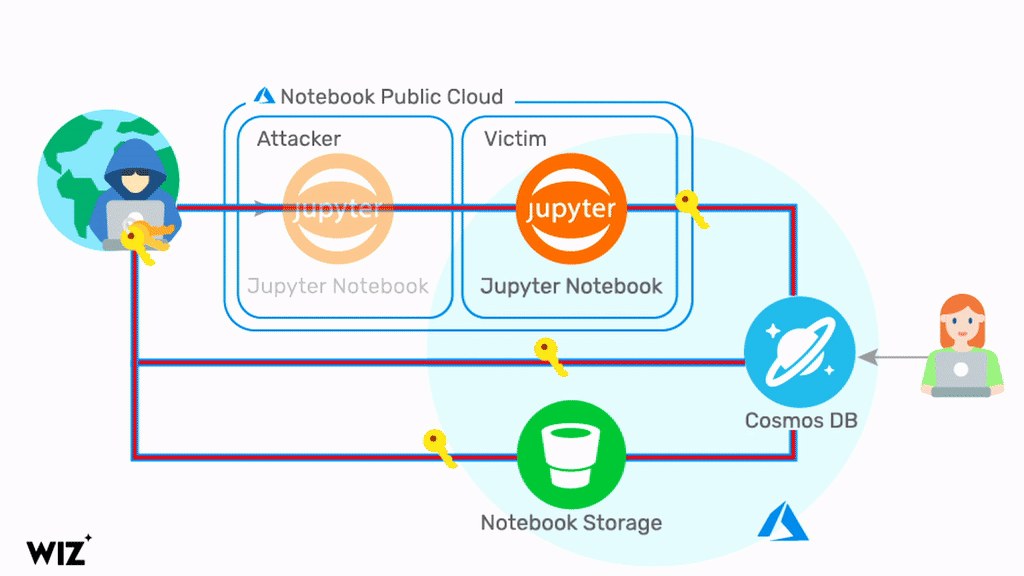
Microsoft’s security teams took an immediate action to fix the problem and disabled the vulnerable feature within 48 hours of the report (see the disclosure timeline below). However, the vulnerability has been exploitable for months and every Cosmos DB customer should assume they’ve been exposed. To mitigate the risk, Microsoft advises customers to regenerate the Cosmos DB Primary Keys. On Aug 26, 2021, Microsoft notified over 30% of Cosmos DB customers about the potential security breach. We believe the actual number of customers affected by #ChaosDB is higher and recommend that all customers follow this guidance.
Microsoft released the following statement to impacted customers: "Microsoft has recently become aware of a vulnerability in Azure Cosmos DB that could potentially allow a user to gain access to another customer's resources by using the account's primary read-write key. This vulnerability was reported to us in confidence by an external security researcher. Once we became aware of this issue on 12 August 2021, we mitigated the vulnerability immediately.
We have no indication that external entities outside the researcher had access to the primary read-write key associated with your Azure Cosmos DB account(s). In addition, we are not aware of any data access because of this vulnerability. Azure Cosmos DB accounts with a vNET or firewall enabled are protected by additional security mechanisms that prevent risk of unauthorized access. Out of an abundance of caution, we are notifying you to take the following actions as a precautionary measure."
Wiz Research Team is a group of experienced researchers who focus on new attack vectors in the cloud. The team finds critical issues and alerts Wiz customers and the community about their findings. In 2021 alone, the team reported dozens of vulnerabilities to cloud service providers like Amazon Web Services, Google Cloud Platform and Microsoft Azure. Their work has been featured at BlackHat (1, 2) and DEFCON (1). Stay tuned for more!
If your organization uses Azure Cosmos DB, then you are likely impacted.
Regenerate your Cosmos DB Primary Key, following the guide provided by Microsoft. We also recommend reviewing all past activity in your Cosmos DB account.
Any Cosmos DB asset that had Jupyter Notebook enabled is potentially impacted.
Microsoft notified only customers that were affected during our short research period (around a week). We think the actual number of potentially impacted customers is much larger and probably includes the majority of Cosmos DB customers, as the vulnerability has been present for months. Our recommendation is to regenerate your Cosmos DB Primary Key for all accounts that had the Jupyter Notebook feature enabled.
Per Microsoft’s request, we are currently not releasing any technical information. We will publish the full technical paper in the near future.
ChaosDB was discovered by @nirohfeld and @sagitz_ from @wiz_io Research Team. If you have questions you can reach us at research@wiz.io.
We don't know.
Yes. See the disclosure timeline.
The Primary Key for the Cosmos DB could be compromised regardless of network access. If the database is not internet facing then the data cannot be accessed remotely.
All Cosmos APIs are exposed in the same way.
Cloud vulnerabilities do not receive CVE-ID. We wanted to create a terminology so that people will be able to reference this vulnerability.
Check out our previous BlackHat talk about this topic
We want to thank Microsoft’s Security Team for springing into action to fix the problem. By disabling the vulnerable entry point feature within 48 hours of receiving the report from Wiz Research Team, they showed a commendable level of care for all impacted users.